Note: As a professional courtesy to those at Adobe who are doing their absolute best to mitigate this breach, I have partially redacted all full hashes and email addresses from this blogpost, besides those found in the image published by arstechnica.com.
We all know about the recent 153 Million account dump from Adobe. As arstechnica showed, the format looks something like this:
Image source: http://arstechnica.com/security/2013/11/how-an-epic-blunder-by-adobe-could-strengthen-hand-of-password-crackers/
As you can see, there's some sort of ID number, the email address, the encrypted password (which from the arstechnica article we now know is 3des) and the password hint.
Password hints are great and all, but they can be unreliable, unclear, or flat out wrong.
HOWEVER, when you have thousands of people using the same password (same encrypted string) looking at all of those password hints together can make the cleartext password painfully obvious.
For example. Let's get the most common encrypted password strings from the dump (with numbers on the left showing how many times they were used):
1911867 EQ7fIp*****=
446144 j9p+********************==
345833 L8qbAD**********CatHBw==
211659 BB4e6X+b*************w==
201569 j9p*****2ws=
124248 dQ*****PYvQ=
113880 7*****Veq8I=
83409 PMDTbP**********FUvYGA==
Now let's take that first, most common password string, and go get all the users' hints who used that same password. Let's also uniq those and sort them by how popular that actual hint is:
One can reasonable guess what password corrisponds with EQ7fIp******=
Now let's see what else we can do with this. Let's use this same method to see if we can target an individual account in the Adobe dump. Funny enough, there's an entry for an account edwardsnowden@******mail.com.
6**58***-|--|-edwardsnowden@******mail.com-|-B***************CatHBw==-|-|--
Now let's see if any other people in the dump have the exact same password hash as this account, and if so then how many.
[jdustin@localhost passwords]$ grep B***************CatHBw== cred | wc -l
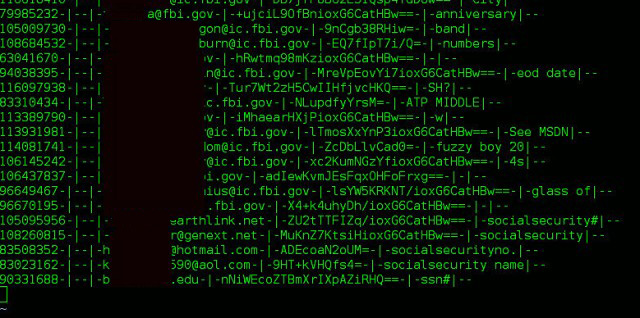
Okay, let's grab those 207 the lines containing all accounts who used that same password, cut out just their password hints, and then sort them by how often that hint is in the list:
[jdustin@localhost passwords]$ grep B***************CatHBw== cred | cut -d"|" -f5 | sort | uniq -c | sort -nr | head -n50
So, Metal? 74W on the table of elements? The usual Tung?
"tungsten" perhaps? Your guess is as good as mine. :)