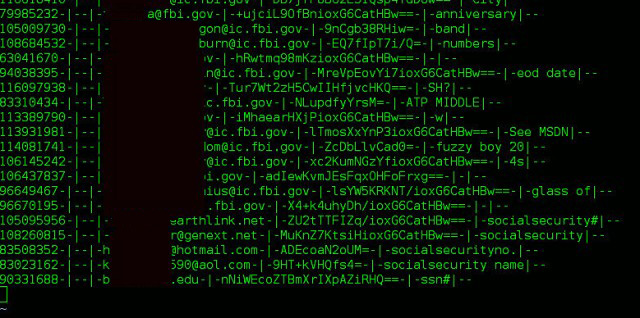
Note: As a professional courtesy to those at Adobe who are doing their absolute best to mitigate this breach, I have partially redacted all full hashes and email addresses from this blogpost, besides those found in the image published by arstechnica.com.
We all know about the recent 153 Million account dump from Adobe. As arstechnica showed, the format looks something like this:
Image source: http://arstechnica.com/security/2013/11/how-an-epic-blunder-by-adobe-could-strengthen-hand-of-password-crackers/
As you can see, there's some sort of ID number, the email address, the encrypted password (which from the arstechnica article we now know is 3des) and the password hint.
Password hints are great and all, but they can be unreliable, unclear, or flat out wrong.
HOWEVER, when you have thousands of people using the same password (same encrypted string) looking at all of those password hints together can make the cleartext password painfully obvious.
For example. Let's get the most common encrypted password strings from the dump (with numbers on the left showing how many times they were used):
1911867 EQ7fIp*****=
446144 j9p+********************==
345833 L8qbAD**********CatHBw==
211659 BB4e6X+b*************w==
201569 j9p*****2ws=
124248 dQ*****PYvQ=
113880 7*****Veq8I=
83409 PMDTbP**********FUvYGA==
Now let's take that first, most common password string, and go get all the users' hints who used that same password. Let's also uniq those and sort them by how popular that actual hint is:
One can reasonable guess what password corrisponds with EQ7fIp******=
Now let's see what else we can do with this. Let's use this same method to see if we can target an individual account in the Adobe dump. Funny enough, there's an entry for an account edwardsnowden@******mail.com.
6**58***-|--|-edwardsnowden@******mail.com-|-B***************CatHBw==-|-|--
Now let's see if any other people in the dump have the exact same password hash as this account, and if so then how many.
[jdustin@localhost passwords]$ grep B***************CatHBw== cred | wc -l
Okay, let's grab those 207 the lines containing all accounts who used that same password, cut out just their password hints, and then sort them by how often that hint is in the list:
[jdustin@localhost passwords]$ grep B***************CatHBw== cred | cut -d"|" -f5 | sort | uniq -c | sort -nr | head -n50
So, Metal? 74W on the table of elements? The usual Tung?
"tungsten" perhaps? Your guess is as good as mine. :)
Friday, November 1, 2013
Tuesday, April 23, 2013
Friday, April 19, 2013
All, I noticed a tweet by HD Moore today giving a shout out to this post written last week by Ed Skoudis. Very good read. Here's a link and an excerpt:
http://pen-testing.sans.org/blog/pen-testing/2013/04/08/when-offense-and-defense-become-one
"at sufficiently advanced technical levels, offense and defense sometimes merge and become one. Offensive techniques can be used to achieve defensive ends; defensive means can be used to achieve offensive ends; and, sometimes, the inherent technical skills of offense and defense are actually identical."
"Consider these examples:
http://pen-testing.sans.org/blog/pen-testing/2013/04/08/when-offense-and-defense-become-one
"at sufficiently advanced technical levels, offense and defense sometimes merge and become one. Offensive techniques can be used to achieve defensive ends; defensive means can be used to achieve offensive ends; and, sometimes, the inherent technical skills of offense and defense are actually identical."
"Consider these examples:
- Endpoint security suites: Have you ever pondered what these tools really are? With their integrated anti-virus, personal firewall, and host-based Intrusion Prevention Systems, they operate at a fairly low-level of most operating systems, hooking all kinds of system calls so that administrators can maintain control of the machine. Wait... that's a rootkit! The only difference between an endpoint security suite and most rootkits is the level of functionality and who controls it: good guy administrators or bad guys. So, we've got a multi-billion dollar segment of the infosec industry that is actually built on selling commercial rootkits, also known as endpoint security suites."
Thursday, January 31, 2013
Habit 1
I gave a presentation at a conference last year, and someone commented that if I have a blog called "the 7 habits of highly effective hackers", I should probably have a list of 7 actual habits on said blog. I guess that's fair.
So here we go starting with habit 1, which I promise will be the only non-technical habit of the 7.
Habit 1: Effective hackers know that the game they play IS the real world.
In a sentence; Effective Hackers understand the repercussions of their actions.
There's something about computer systems that causes many people to act in a way that they never would in real life. Some of us would never read a stranger's physical mail, yet would feel no guilt whatsoever about reading their email. We make silly excuses to justify why our online world is different than our real world. That person should have changed the default password on their router; they're stupid and deserve it. That company knows their environment/product is insecure, if they wanted to keep me out they'd have fixed it.
Think this one over. Although there's no CVE number for it yet, it is now being reported that human beings are vulnerable to having bricks thrown at their heads. All versions are affected, and easy methods for exploiting this weakness have reportedly been in the wild for some time now....Would anyone think that the public disclosure of this knowledge, would in any way justify them throwing bricks, and hurting others? Are we more justified because they should have known better?
This probably all sounds really preachy. I'm actually not trying to tell you that you should feel guilt for hurting others (that's between you and your own conscience). I AM trying to say you should understand the repercussions of your actions. If you post someone's PII on pastebin, someone, A REAL PERSON, will experience real grief over it. When you gain access to someone's network, it could mean real impact for that organization. Real people could lose their jobs over it. I'm not telling you to care, I'm telling you that you MUST understand.
You must do whatever you do with your eyes wide open. Know and accept all possible impacts of every scan, every exploit, every move.
Okay, gotta go. My shirt just got out of the dryer. I'm sure we're all familiar with MITM (Mythbuster In The Middle).
So here we go starting with habit 1, which I promise will be the only non-technical habit of the 7.
Habit 1: Effective hackers know that the game they play IS the real world.
In a sentence; Effective Hackers understand the repercussions of their actions.
There's something about computer systems that causes many people to act in a way that they never would in real life. Some of us would never read a stranger's physical mail, yet would feel no guilt whatsoever about reading their email. We make silly excuses to justify why our online world is different than our real world. That person should have changed the default password on their router; they're stupid and deserve it. That company knows their environment/product is insecure, if they wanted to keep me out they'd have fixed it.
Think this one over. Although there's no CVE number for it yet, it is now being reported that human beings are vulnerable to having bricks thrown at their heads. All versions are affected, and easy methods for exploiting this weakness have reportedly been in the wild for some time now....Would anyone think that the public disclosure of this knowledge, would in any way justify them throwing bricks, and hurting others? Are we more justified because they should have known better?
This probably all sounds really preachy. I'm actually not trying to tell you that you should feel guilt for hurting others (that's between you and your own conscience). I AM trying to say you should understand the repercussions of your actions. If you post someone's PII on pastebin, someone, A REAL PERSON, will experience real grief over it. When you gain access to someone's network, it could mean real impact for that organization. Real people could lose their jobs over it. I'm not telling you to care, I'm telling you that you MUST understand.
You must do whatever you do with your eyes wide open. Know and accept all possible impacts of every scan, every exploit, every move.
Okay, gotta go. My shirt just got out of the dryer. I'm sure we're all familiar with MITM (Mythbuster In The Middle).
Subscribe to:
Posts (Atom)